The Enterprise AI Challenge → Transparency
→ Control → Insight
Shadow AI
Employees using AI apps without oversight
Chatbots
Inappropriate and incorrect responses
Data
Handling and securing sensitive information
Compliance
Adhering to regulations and avoiding violations
Reputation
Maintaining trust and ethical practices
Evolution
Continuous development of new AI models
8th Layer of Security
Traditional 7 Layers
- Human Layer
- Perimeter Layer
- Network Security
- Enpoint Security
- Application Security
- Data Security
- IAM
AI Integrity Layer
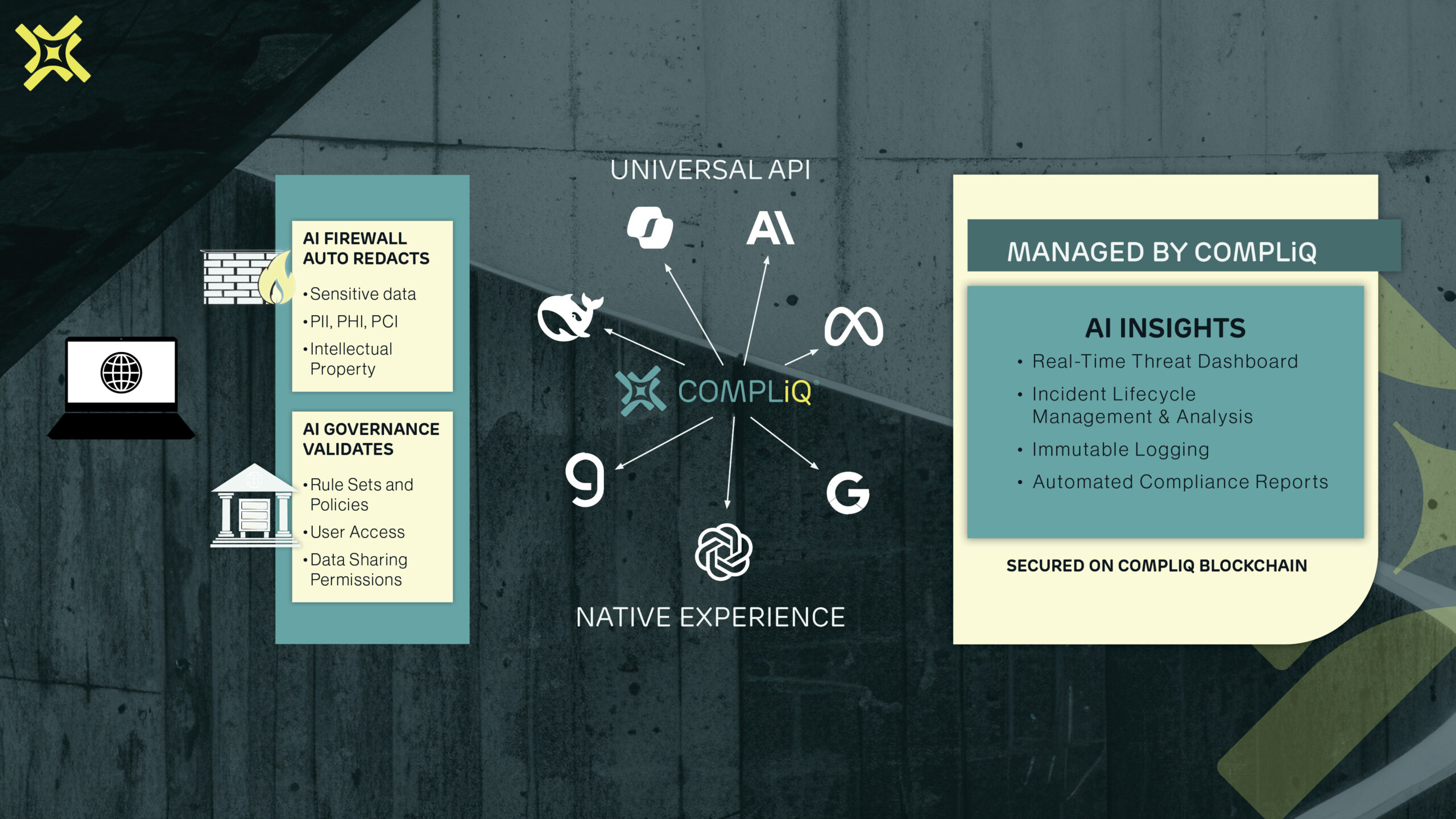
- AI Firewall
- AI SIEM
- AI Insights
Top Use Cases
- Secure Copilot
- Block PII in AI Models
- Comply with AI Regulations
- Keep Intellectual Secrets Safe
Solution Overview
Launchpad to Success
1
Assess Capabilities
Evaluate your current AI readiness and identify opportunities.
2
Use Case Planning
Define high-impact AI applications tailored to your business,
3
Solution Architecture
Design a scalable, secure, and compliant AI infrastructure.
4
Threat Evaluation
Identify and mitigate potential vulnerabilities in your AI system.
5
Risk & Compliance
Assess your preparedness and create a mitigation plan.
6
ROI Analysis
Prove the value of your AI investment with real-world pilot tests.
7
Implementation
Roadmap-develop a detailed plan for integrating COMPLiQ and Intercept solutions into your operations.
